Hipaa Risk Assessment Template Excel
Risk analysis is defining the whole shape of your information security make sure you do it right.
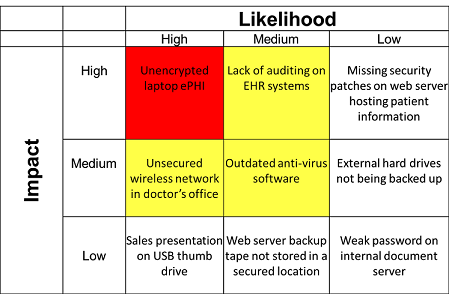
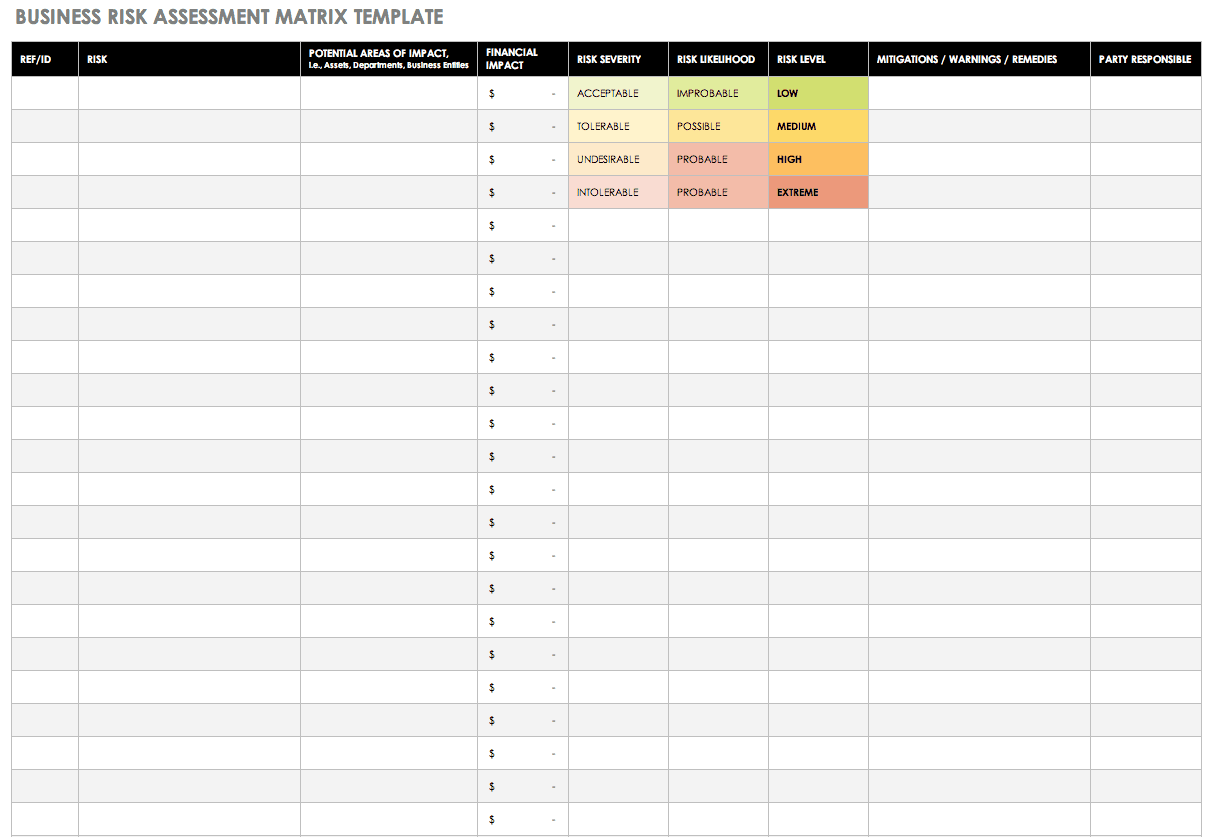
Hipaa risk assessment template excel. Conduct an accurate and thorough assessment of the potential risks and vulnerabilities to the confidentiality integrity and availability of electronic protected health information held by the covered entity or business associate. Hhs onc security risk assessment tool hipaa security rule toolkit posting excel spreadsheets of the office of the national coordinator for health information technology onc security risk assessment sra. A risk assessment also helps reveal areas where your organizations protected health information phi could be at risk. Hipaa risk and security assessments give you a strong baseline that you can use to patch up holes in your security infrastructure.
The health insurance portability and accountability act hipaa security rule requires that covered entities and its business associates conduct a risk assessment of their healthcare organization. B risk management required. The health insurance portability and accountability act of 1996 hipaa requires that you perform a periodic risk assessment of your practice. A risk assessment is a mandatory analysis of your practice that identifies the strengths and weaknesses of the safeguards your practice has in place to protect patient information and privacy.
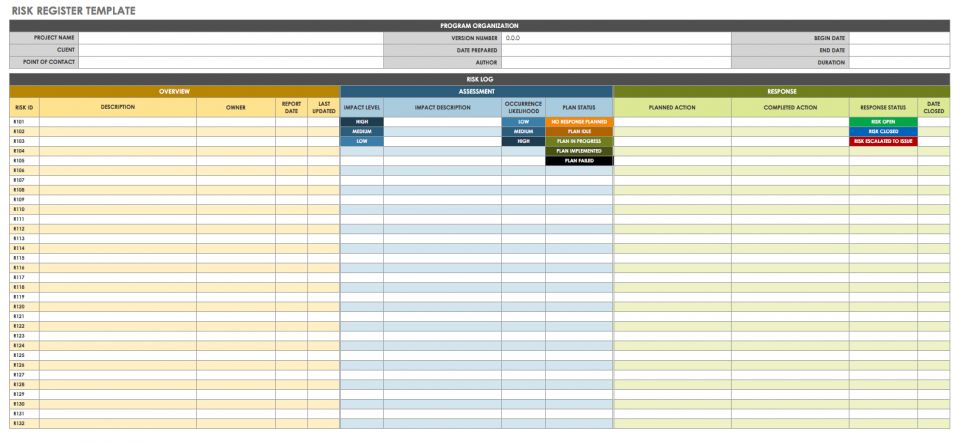
The hipaa cow risk management networking group reviewed the established performance criteria and audit procedures in the ocr hipaa audit program and enhance the hipaa security questions and recommended controls on the hipaa cow risk assessment template spreadsheet. Guidance on risk analysis. A hipaa risk assessment is an essential component of hipaa compliance. This is especially true if one were to handle protected health information.
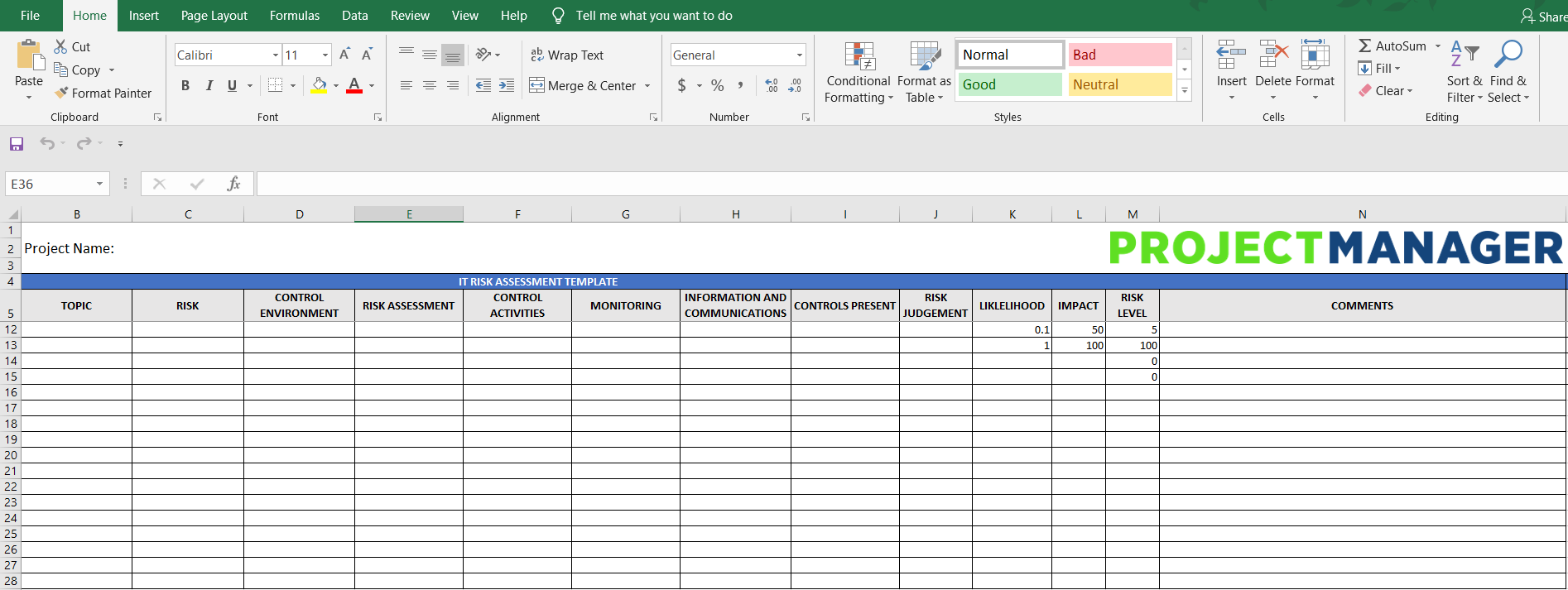
The nist hipaa security toolkit application developed by the national institute of standards and technology nist is intended to help organizations better understand the requirements of the hipaa security rule implement those requirements and assess those implementations in their operational environment. A risk assessment helps your organization ensure it is compliant with hipaas administrative physical and technical safeguards. Received maintained or transmitted by the cehrt for a risk analysis to also be compliant with hipaa security rule requirements risks must be identified and assessed for all of the e phi the practice creates receives maintains or transmits. Guidance on risk analysis requirements under the hipaa security rule.
Risk analysis the examination of assets their threats and vulnerabilities to identify and evaluate risks. Guidance on risk analysis. 3 hipaa security risk analysis templates pdf if you were to obtain confidential information then you would want to do everything you can to ensure that its secure.