Information Security Email Template

Top 10 anti phishing email templates 1.
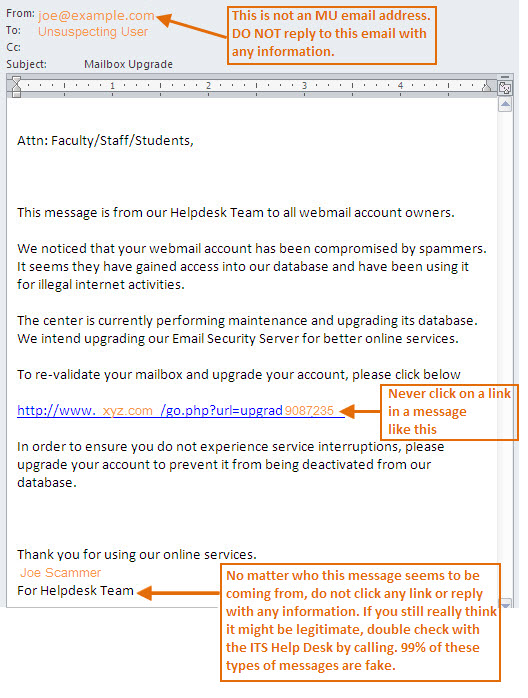
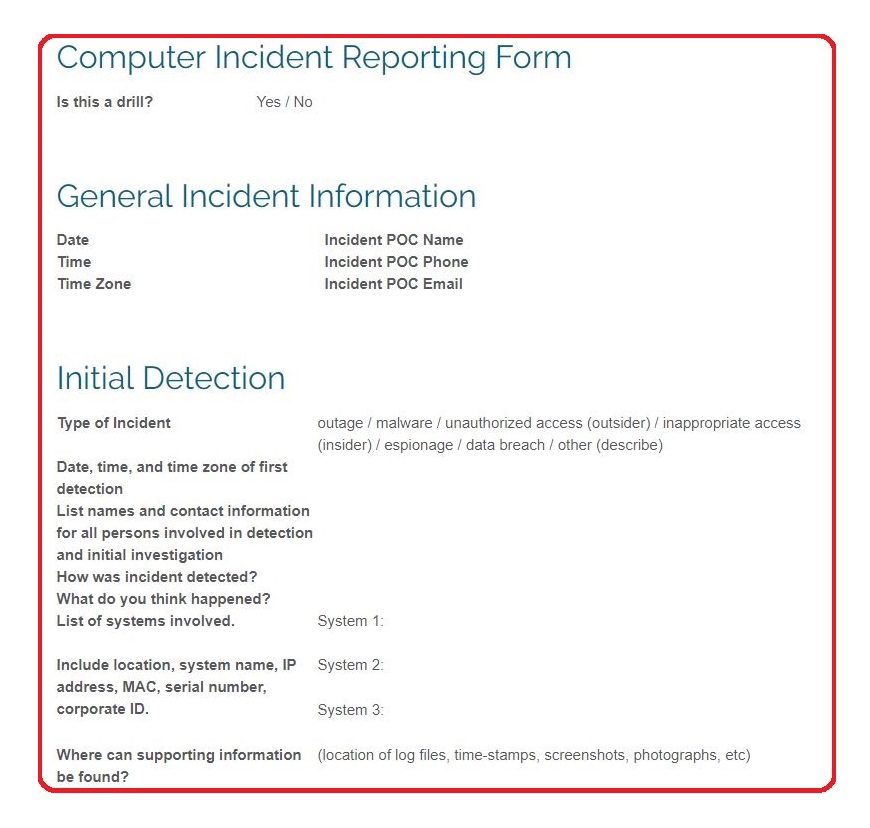
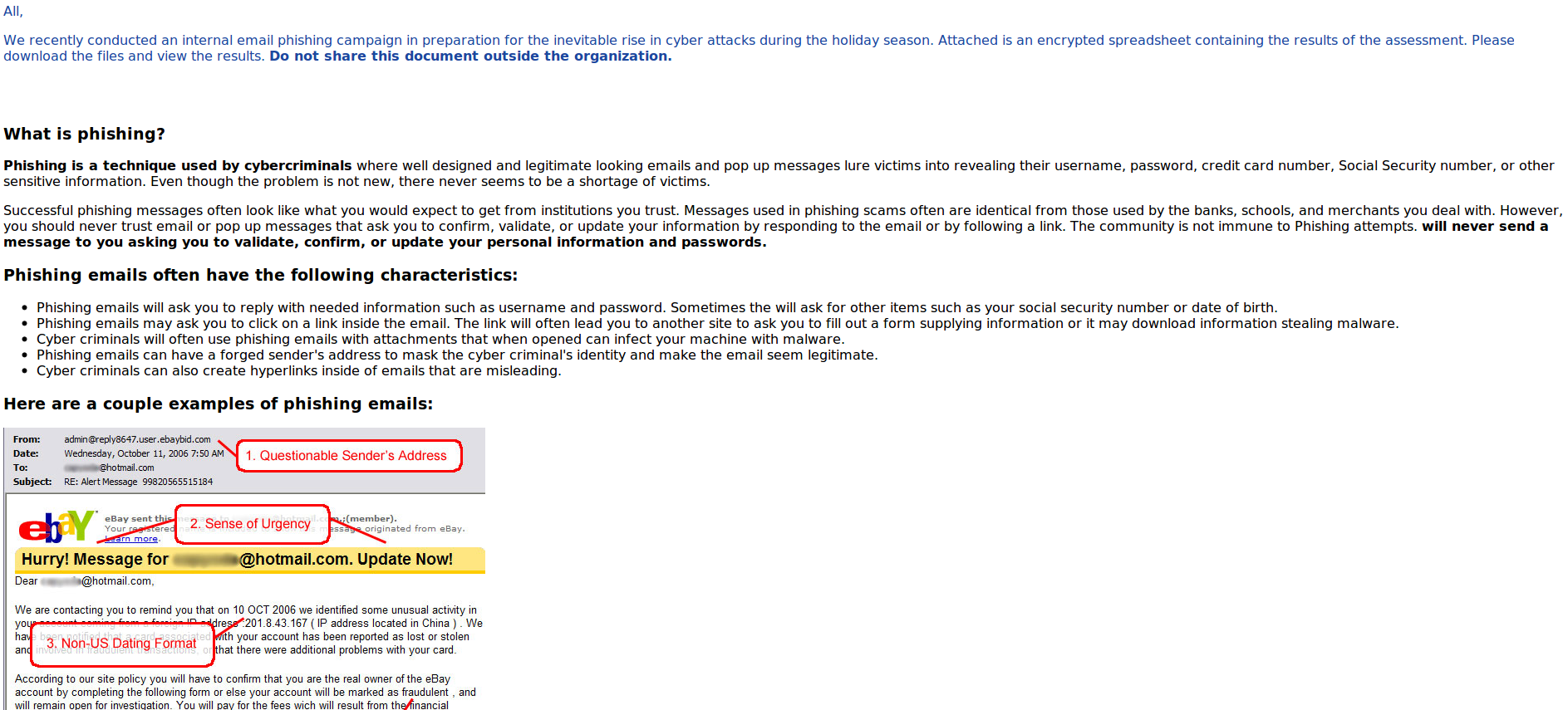
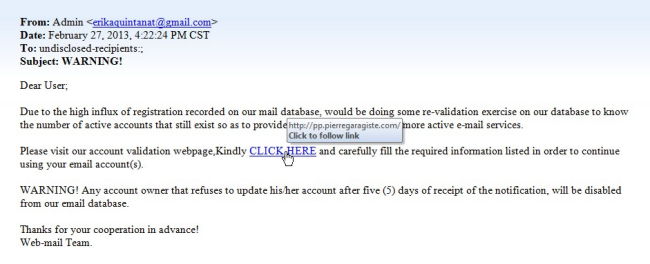
Information security email template. Just copy the text into your favorite word processor and customize it to fit your needs. A well written security policy should serve as a valuable document of instruction. An information security policy forces you to think through and address all of the ways that data is handled in your business. Share this item with your.
More importantly it outlines how youll keep your data safe even though there are thousands of ways that it could be breached. Please note that any bracketed text is meant to be replaced with your company specific information. The prevention of wastes. Sample e mail policy template and checklist of concerns kevin beaver provides a simple template approach for writing e mail security policies and a checklist of concerns.
A good information security policy template should address these concerns. Feel free to use share and remix. Elimination of potential legal liabilities. The protection of the valuable information of the organization.
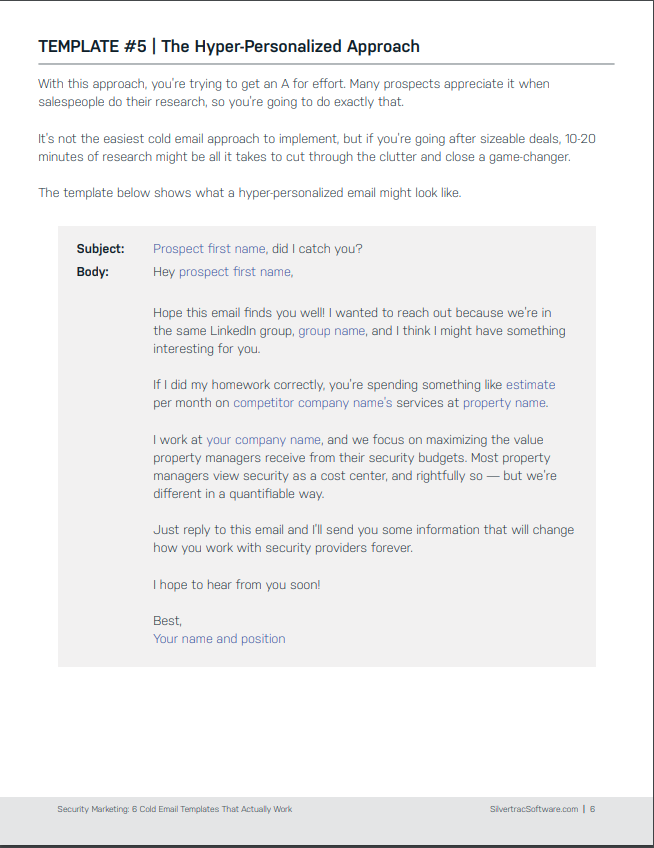
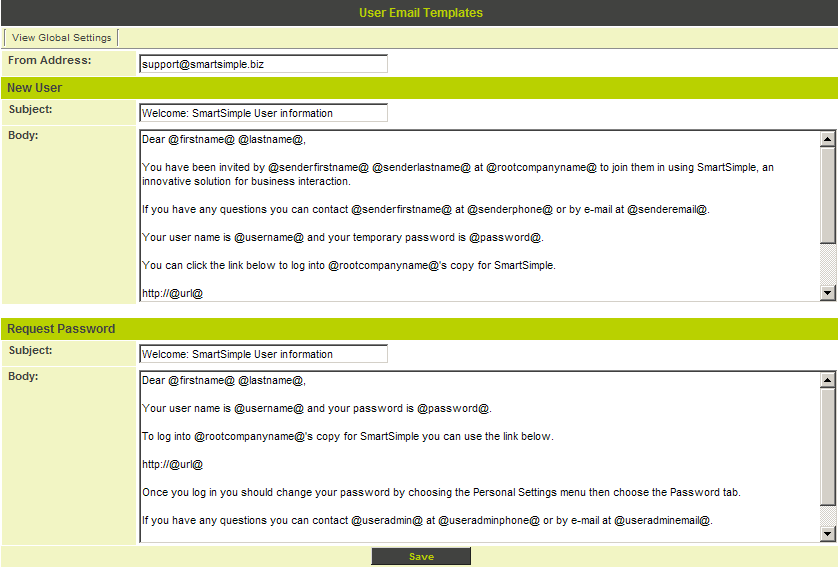
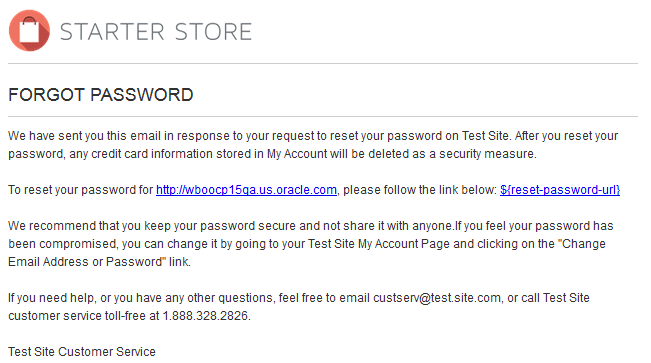
Information security policy templates subscribe to sans newsletters join the sans community to receive the latest curated cyber security news vulnerabilities and mitigations training opportunities and our webcast schedule. The ultimate goal of the project is to offer everything you need for rapid development and implementation of information security policies. Below you can find email templates for the four most common cyber awareness topics. Your order has shipped.
Welcome to the sans security policy resource page a consensus research project of the sans community. Information security policy templates. The inappropriate use of the resources of the organization. Youll find a great set of resources posted here already.
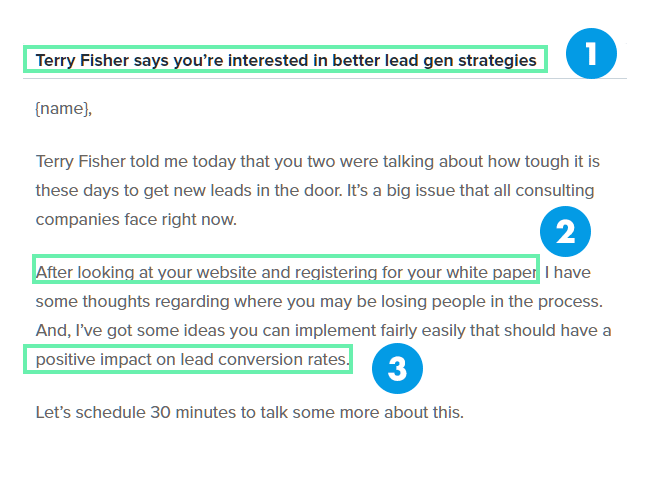
Then paste it into an email for distribution to the appropriate recipients. This template package can help take some of the effort out of writing and rewriting those emails. A security policy template enables safeguarding information belonging to the organization by forming security policies. In any organization a variety of security issues can arise which may be due to improper information sharing data transfer damage to the property or assets breaching of network security etc.