Kubernetes Ca Certificate

Kubeadm alpha certs renew provides the following options.
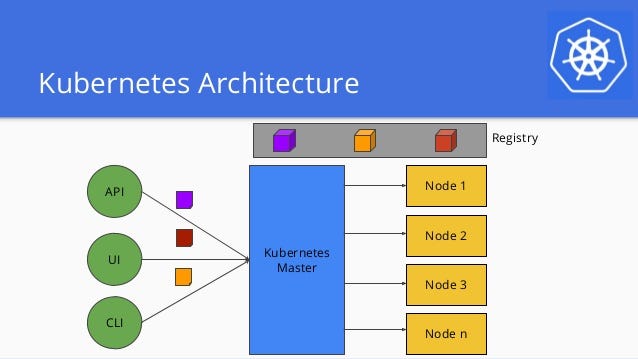
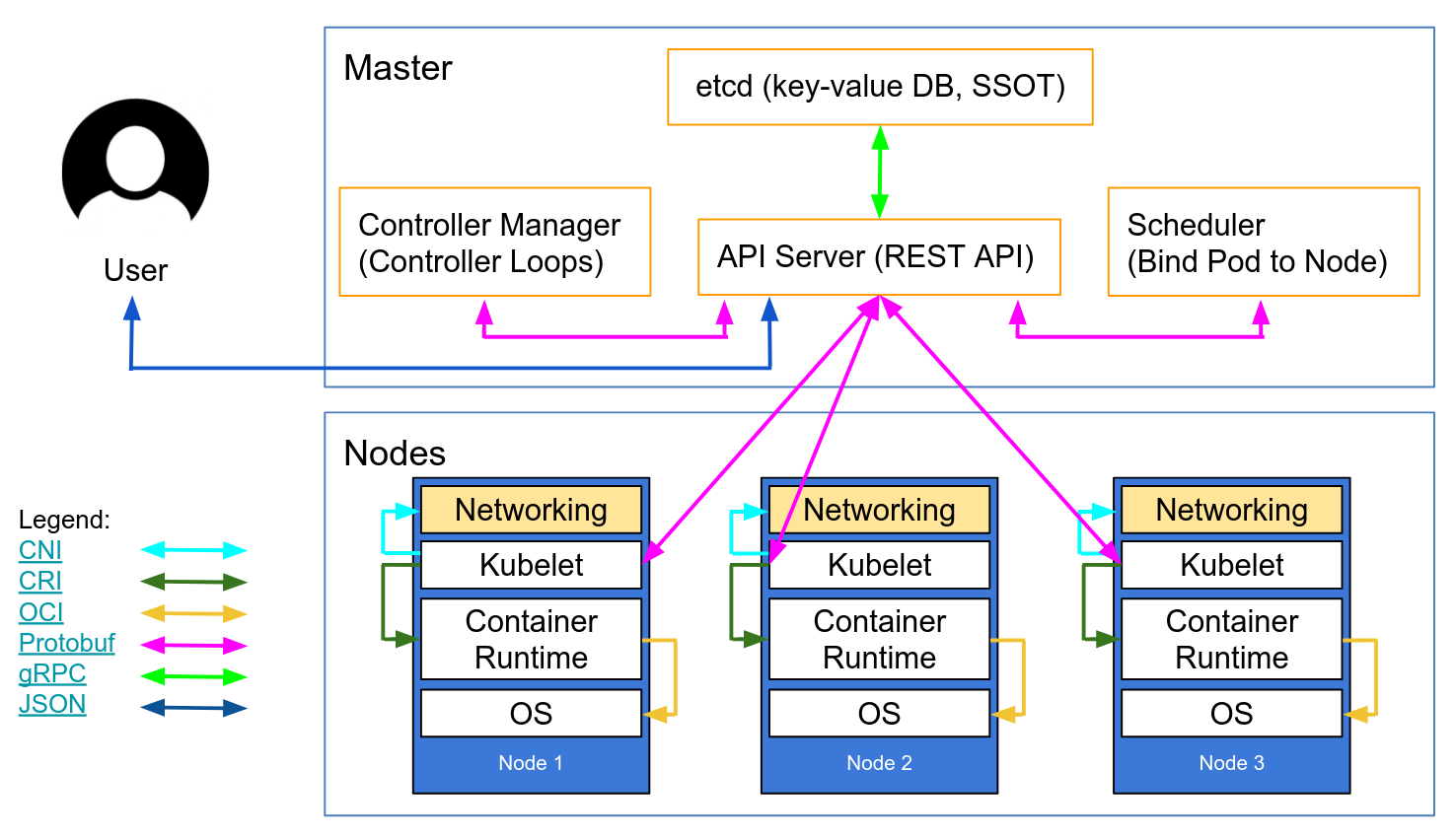
Kubernetes ca certificate. Generate the kubernetes api server certificate and private key. If you install kubernetes with kubeadm certificates are stored in etckubernetespkiall paths in this documentation are relative to that directory. The kubernetes certificates normally reach their expiration date after one year csr only can be used to renew certificates with an external ca by generating certificate signing requests without actually renewing certificates in place. As http requests are made to the api server plugins attempt to associate the following attributes with the request.
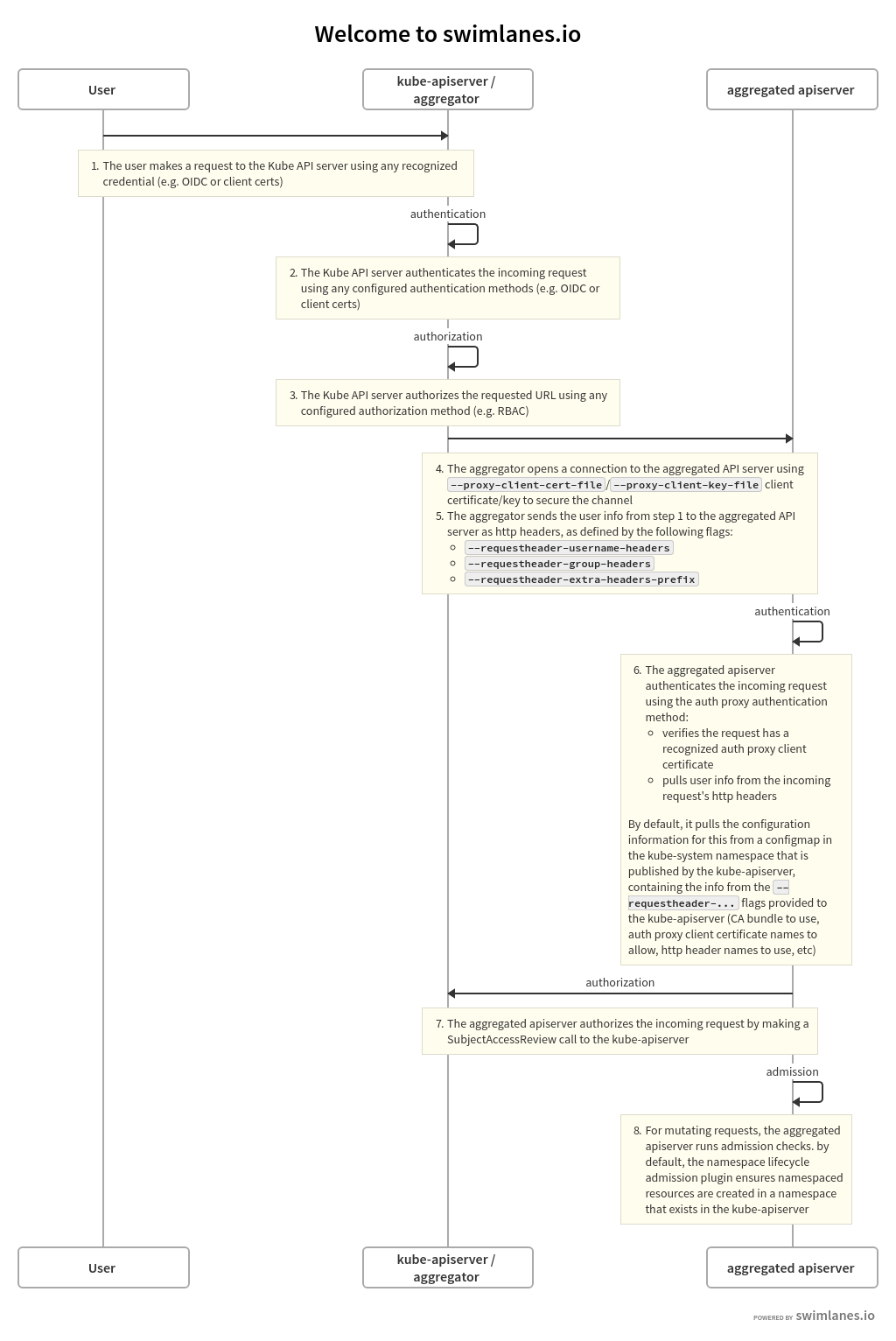
Kubernetes uses client certificates bearer tokens an authenticating proxy or http basic auth to authenticate api requests through authentication plugins. See next paragraph for more information. The kubernetes the hard way static ip address will be included in the list of subject alternative names for the kubernetes api server certificate. And it should be securely stored.
Etcd certfile string ssl certification file used to secure etcd communication. The cakey is used by the ca for signing certificates. Etcd also implements mutual tls to authenticate clients and peers. You will use the cacrt file in many places so it will be copied to many places.
The cacrt is the kubernetes certificate authority certificate and cakey is the kubernetes certificate authority private key. The kubernetes api server certificate. Distributing self signed ca certificate. For a non production deployment or for a deployment that runs behind a company firewall you can distribute a self signed ca certificate to all clients and refresh the local list for valid certificates.
In the next step you generate a kubernetes secret using the tls certificate and private key generated by openssl. The following example generates a 2048 bit rsa x509 certificate valid for 365 days named aks ingress. Its also possible to renew a single certificate. Where certificates are stored.
Default varrunkubernetes client ca file string if set any request presenting a client certificate signed by one of the authorities in the client ca file is authenticated with an identity corresponding to the commonname of the client certificate. Your app in kubernetes pod is relaying on an certificate which is not in truest root ca store then here is how you can add that. A client node may refuse to recognize a self signed ca certificate as valid.