Pki Digital Certificates
A pki environment assigns a digital identity for all your employees and machines allowing for secure access to data networks and physical locations.
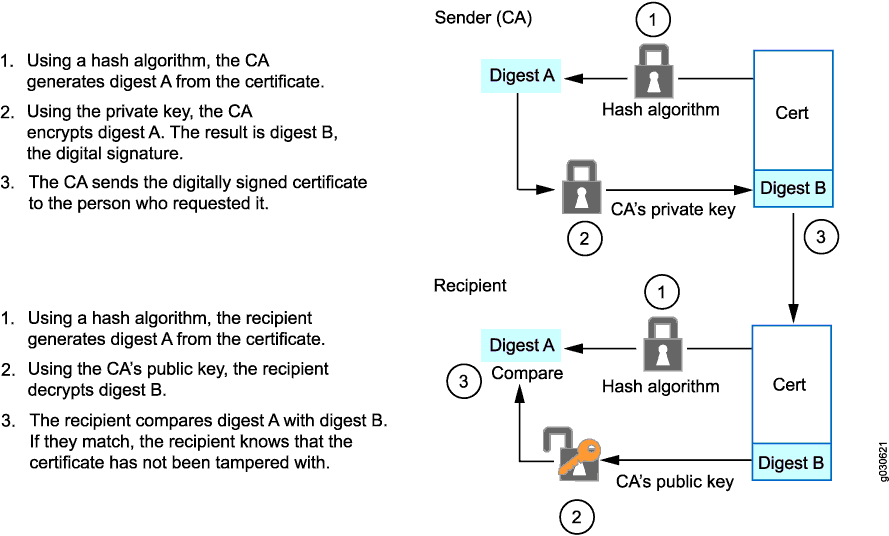
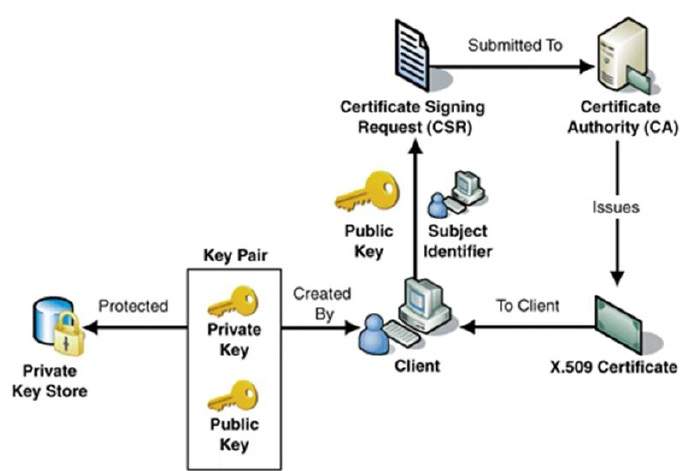
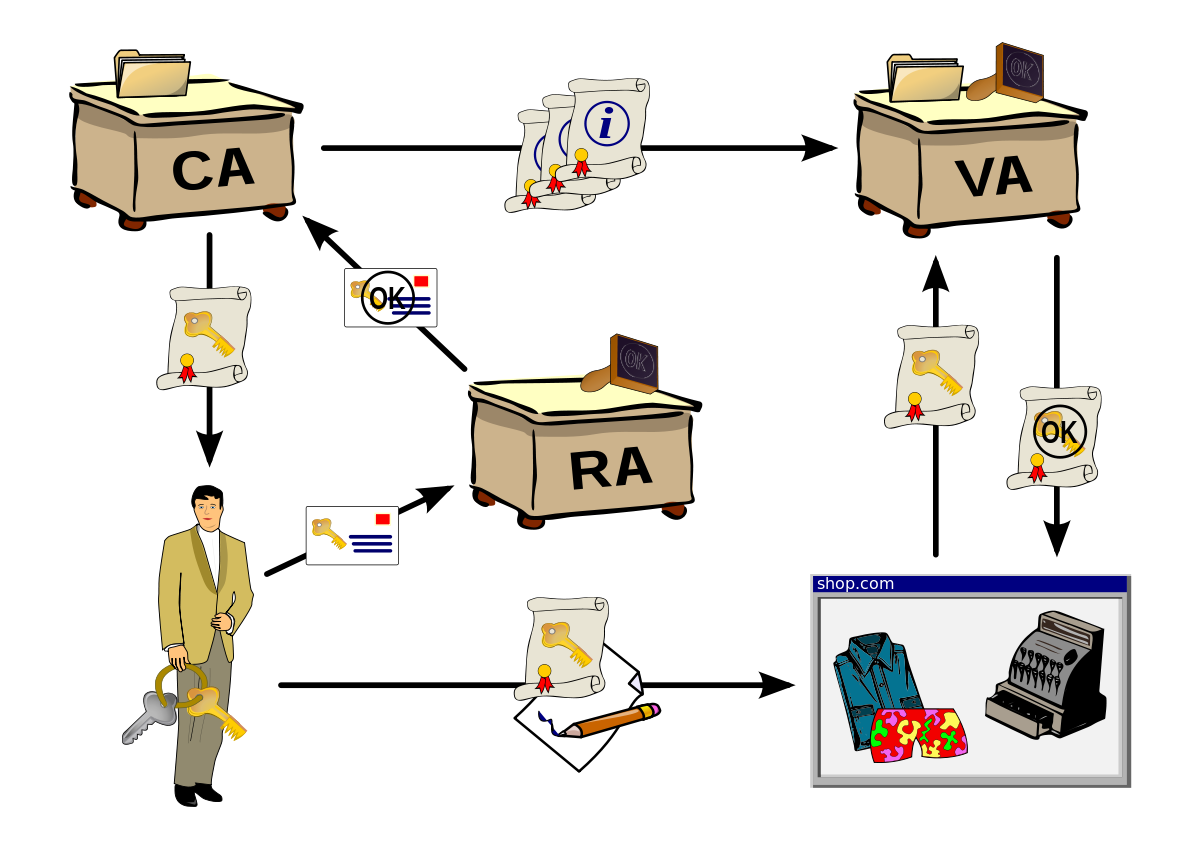
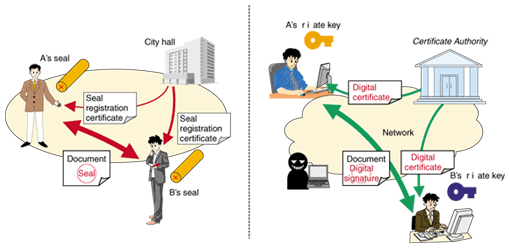
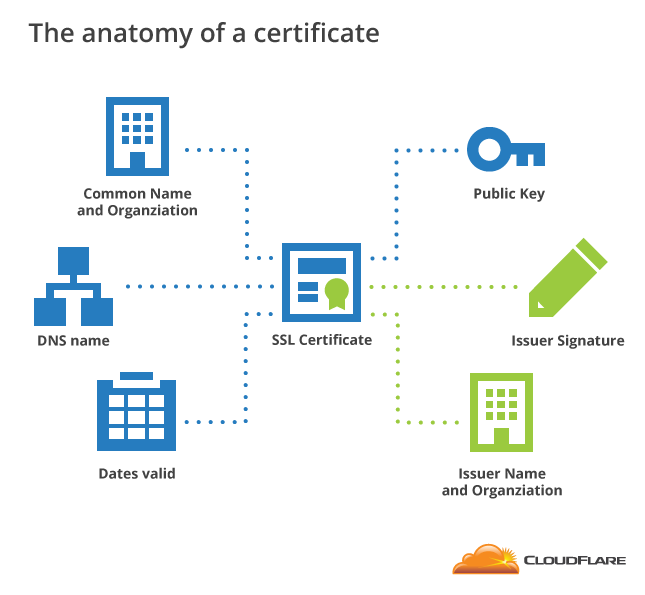
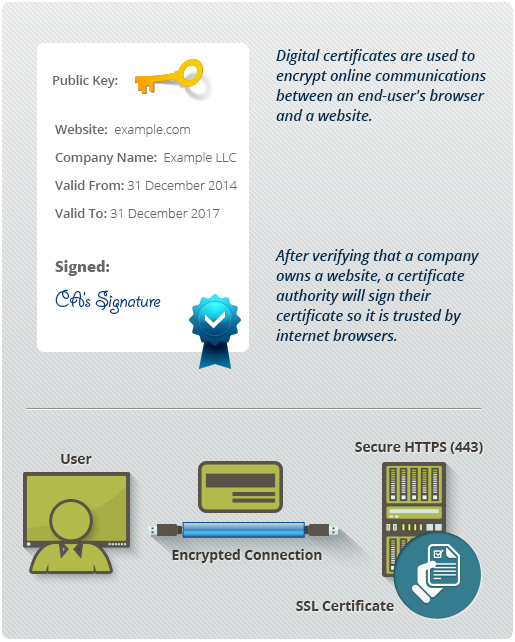
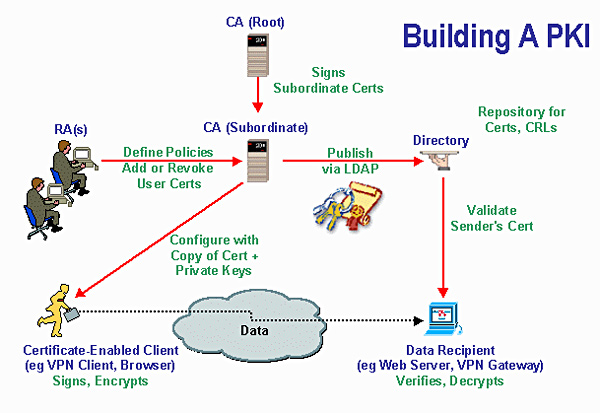
Pki digital certificates. Digital certificate is also known as a public key certificate or identity certificate. A digital certificate is an electronic password that allows a person organizaion to exchange data securely over the internet using the public key infrastructure pki. A public key infrastructure pki is a system for the creation storage and distribution of digital certificates which are used to verify that a particular public key belongs to a certain entity. The pki creates digital certificates which map public keys to entities securely stores these certificates in a central repository and revokes them if needed.
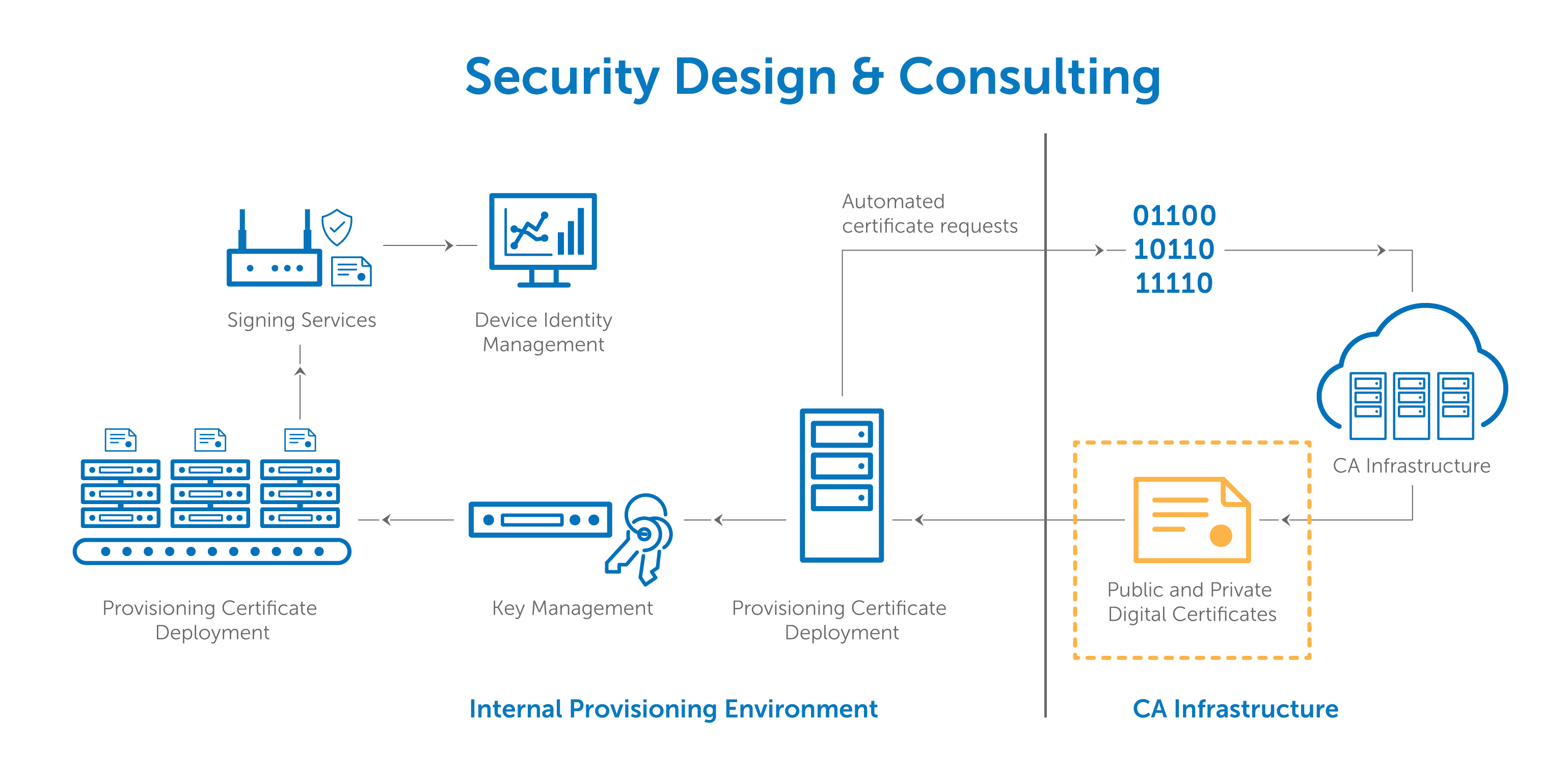
Digital certificatespki for ipsec vpns this document provides information about using x509 digital certificates issued by a cisco ios ca server to authenticate vpn tunnels between cisco routers. A pki enables the use of encryption and digital signature services across a wide variety of applications. The pki environment includes credential management solutions for complete lifecycle administration of certificates and permissions. An organization that maintains a pki and manages the issuance and revocation of digital certificates is known as a certificate authority ca.
By enabling authenticity integrity and encryption pki and digital certificates permit secure communication over insecure networks such as the internet. The system allows users to swap information securely across a public network through a pair of public and private cryptographic keys which is obtained and accessed through a certificate authority ca. Learn how pki plays a critical role in keeping devops environments safe. The purpose of a public key infrastructure is to manage keys and certificates.
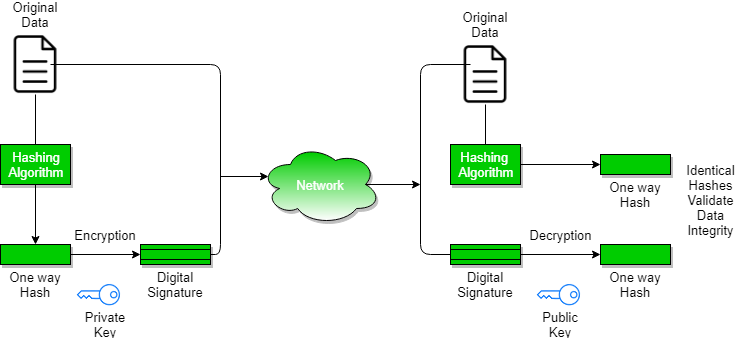
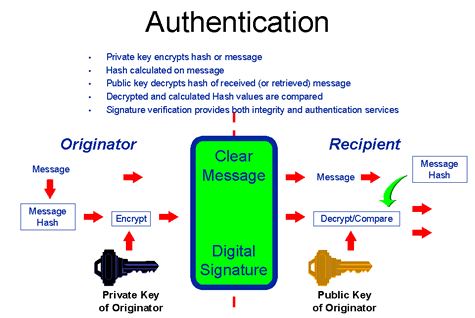
Whether pki digital certificates are used to encrypt data and ensure privacy to digitally sign documents and messages to attest to their integrity and authenticity or to authenticate users and systems and control access these public key operations are integral to modern operating systems commercial security products and custom built systems.