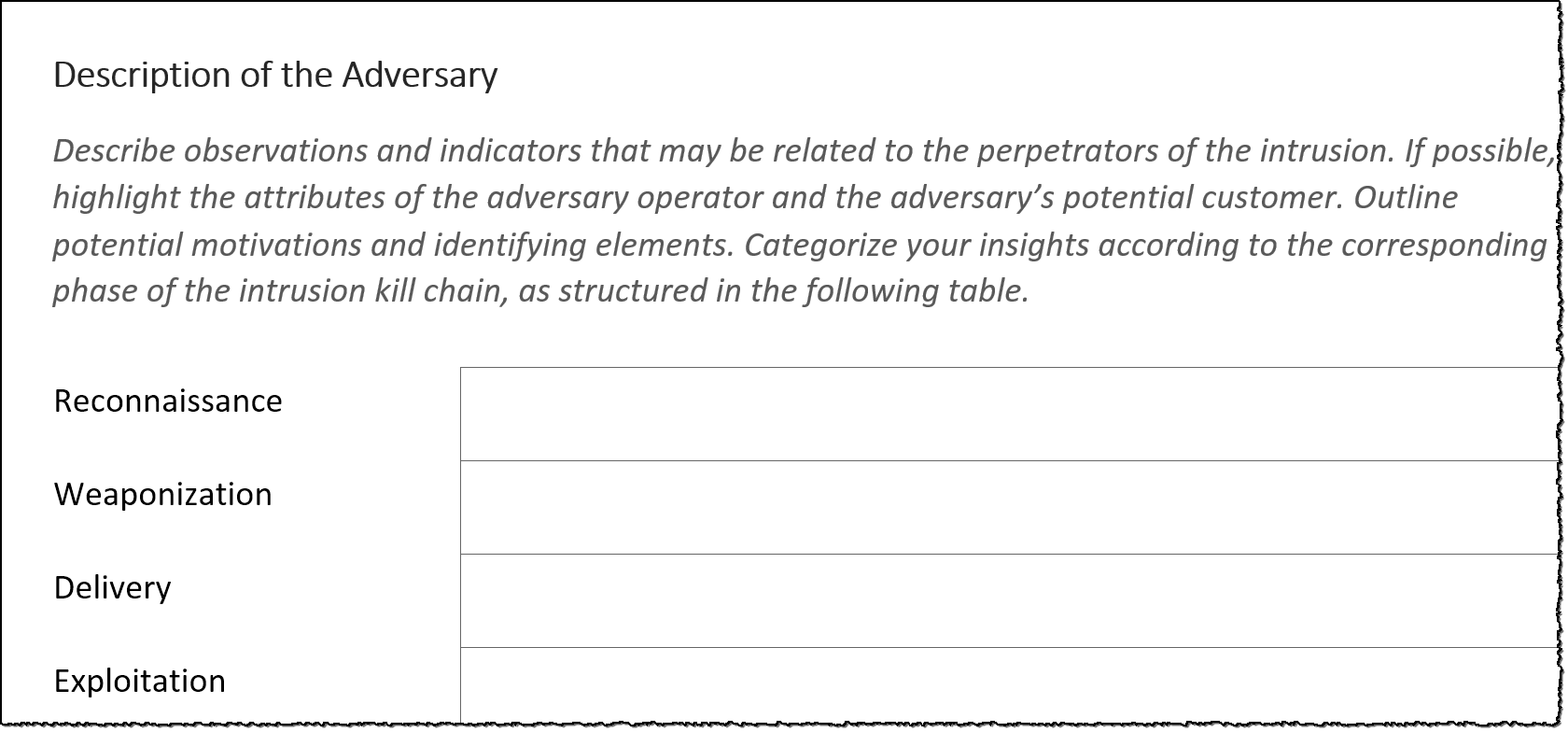
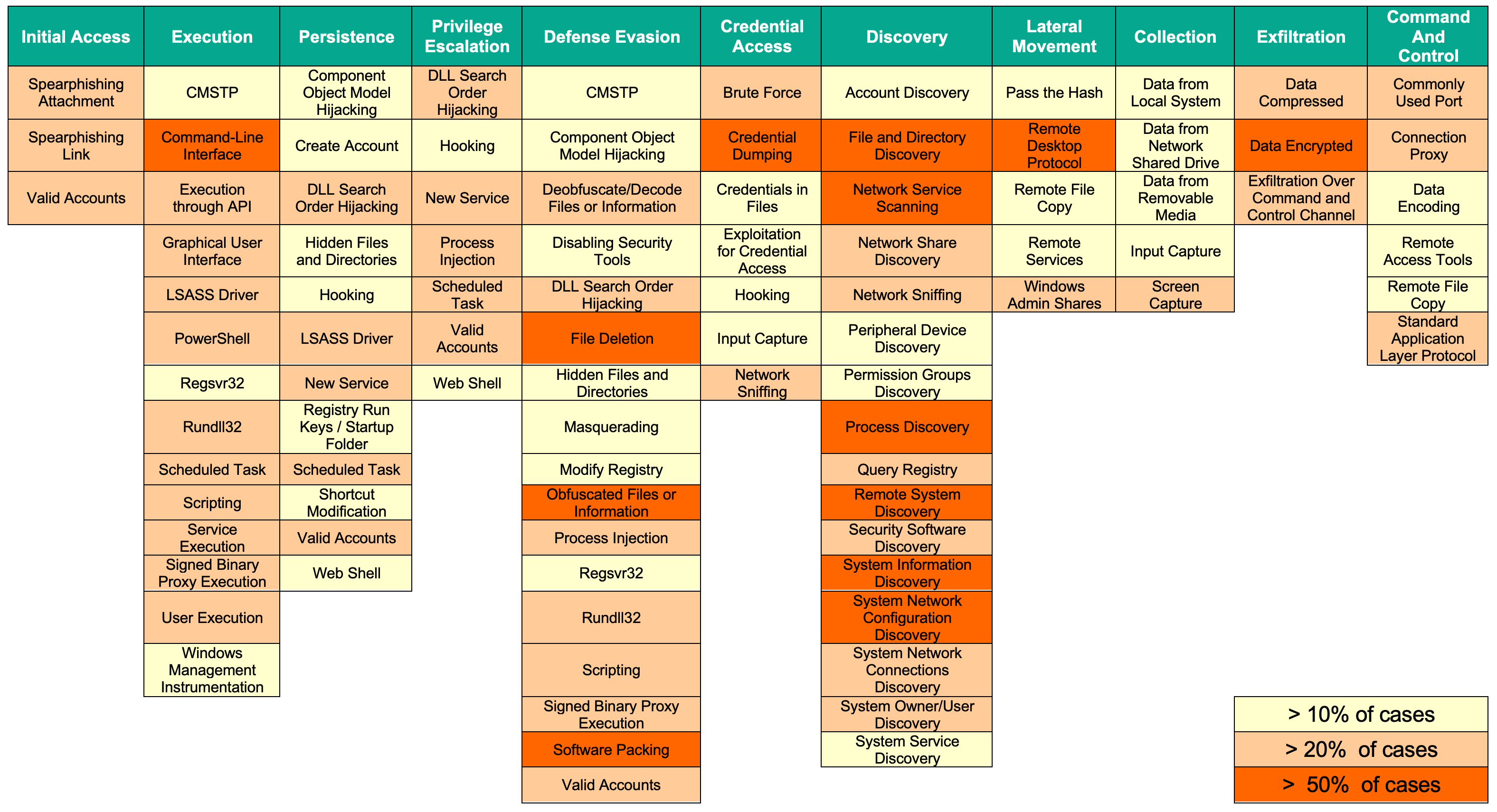
Threat Hunting Report Template
Thret hnting report 6 threat hunting priority q.
Threat hunting report template. This report confirms that threat hunting pays off with earlier detection faster response and denial of future exploits. Weekly threat intelligence report template. Nearly four out of five respondents said that threat hunting should be or will be a top security initiative in 2017 with 42 saying that they strongly agreed with the. Download now and uncover key findings such as.
Monday mornings mark the start of a new week with a new set of cybersecurity topics and issues for employees across all teams to review and discuss. Report template for threat intelligence and incident response. Threat hunting report template. When handling a large scale intrusion incident responders often struggle with obtaining and organizing the intelligence related to the actions taken by the intruder and the targeted organization.
They can then be reused in some cases with minor adaptations as a foundation for creating new threat models. Threat model templates reusability and efficiency. This project provides not only information about. Threat hunting is the process of seeking out adversaries before they can successfully execute an attack.
Report template ir report template. March 5 2019 parker crucq. There were more than 90 ventures being exhibited and our own was. The concept of hunting for threats is not new but many organizations are putting an increased emphasis on programmatic threat hunting in recent times due to malicious actors increasing ability to evade traditional detection methods.
Based on a comprehensive survey of cybersecurity professionals in the 400000 member information security community on linkedin the 2018 threat hunting report reveals that cyber threats continue to rise dramatically. The threat hunter playbook is a community based open source project developed to share threat hunting concepts and aid the development of techniques and hypothesis for hunting campaigns by leveraging security event logs from diverse operating systems. Threat model templates enable architects developers and security analysts to take commonly used threat models and save them as templates. And to read the latest from cybereason about threat hunting check out the 2017 threat hunting survey report.
Ir report template i adored the rush of certifiable models being displayed live. As a result more organizations are moving away from traditional reactive security while incorporating threat hunting techniques in their cybersecurity strategy. If you decide to conduct a threat hunting exercise you first need to decide whether to use your internal security team or outsource it to an external threat hunting service provider.